什么是http rbac filter
rbac是基于角色的权限控制,http rbac filter是envoy中http类型的权限控制过滤器。我们istio中常用的权限控制资源AuthorizationPolicy,底层就是通过rbac filter实现的。rbac filter 名称为envoy.filters.http.rbac,type固定名称为type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC。rbac filter有两种类型,一种是network过滤器,还有一种是http过滤器,本往篇讲的是http类型的rbac。
配置说明
{ "rules": "{...}", "shadow_rules": "{...}", "shadow_rules_stat_prefix": "..." }rules: 配置规则
shadow_rules:规则不生效,但会记录日志
shadow_rules_stat_prefix:影子规则的stat前缀
rules:
{ "action": "...", "policies": "{...}" }action:动作,可以是ALLOW,DENY,LOG
policies:策略配置,包括主体和权限,条件
policies:
{ "permissions": [], "principals": [], "condition": "{...}" }permissions:权限配置
principals:主体配置
condition:条件配置
permissions:
{ "and_rules": "{...}", "or_rules": "{...}", "any": "...", "header": "{...}", "url_path": "{...}", "destination_ip": "{...}", "destination_port": "...", "destination_port_range": "{...}", "metadata": "{...}", "not_rule": "{...}", "requested_server_name": "{...}" }and_rules:每个权限都必须满足
or_rules:至少一个权限满足
any:任意权限
header:请求头
url_path:url路径
destination_ip:目标ip
destination_port:目标端口
destination_port_range:目标端口范围
metadata:元数据
not_rule:必须不满足的权限
requested_server_name:请求服务主机名
principals:
{ "and_ids": "{...}", "or_ids": "{...}", "any": "...", "authenticated": "{...}", "source_ip": "{...}", "direct_remote_ip": "{...}", "remote_ip": "{...}", "header": "{...}", "url_path": "{...}", "metadata": "{...}", "not_id": "{...}" }and_ids:与id,必须都满足主体
or_ids:或id,至少满足一个主体
any:任意主体
authenticated:认证过的主体
source_ip:来源ip
direct_remote_ip:直接远程地址
remote_ip:远程地址
header:请求头
url_path:请求路径
metadata:元数据
not_id:必须不能满足的主体
用rbac filter实现权限控制
allow nothing
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: allow-nothing
spec:
{}envoyfilter实现方式
cat << EOF > ef-allow-nothing.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[allow-nothing]-rule[0]:
permissions:
- notRule:
any: true
principals:
- notId:
any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-allow-nothing.yaml -n istio --context context-cluster1清理:
kubectl delete -f ef-allow-nothing.yaml -n istio --context context-cluster1名称空间拒绝所有
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: deny-all
spec:
action: DENY
# This matches everything.
rules:
- {}envoyfilter实现
cat << EOF > ef-deny-all.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
action: DENY
policies:
ns[istio]-policy[deny-all]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-deny-all.yaml -n istio --context context-cluster1清理:
kubectl delete -f ef-deny-all.yaml -n istio --context context-cluster1名称空间允许所有
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: allow-all
spec:
action: ALLOW
rules:
- {}envoyfilter实现
cat << EOF > ef-allow-all.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[allow-all]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-allow-all.yaml -n istio --context context-cluster1from-principals
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- from:
- source:
principals: ["cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"]envoyfilter实现
cat << EOF > ef-from-principals.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
exact: spiffe://cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account
EOF
kubectl apply -f ef-from-principals.yaml -n istio --context context-cluster1from-notPrincipals
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- from:
- source:
notPrincipals: ["cluster.local/ns/istio-system/sa/test"]envoyfilter实现
cat << EOF > ef-from-notprincipals.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- authenticated:
principalName:
exact: spiffe://cluster.local/ns/istio-system/sa/test
EOF
kubectl apply -f ef-from-notprincipals.yaml -n istio --context context-cluster1from-requestPrincipals
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- to:
- operation:
notPaths: ["/healthz"]
from:
- source:
requestPrincipals: ["*"]envoyfilter实现
cat << EOF > ef-from-requestPrincipals.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- urlPath:
path:
exact: /healthz
principals:
- andIds:
ids:
- orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.principal
value:
stringMatch:
safeRegex:
googleRe2: {}
regex: .+
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-requestPrincipals.yaml -n istio --context context-cluster1from-notRequestPrincipals
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- to:
- operation:
paths: ["/productpage"]
from:
- source:
notRequestPrincipals:
- "testing@secure.istio.io/testing@secure.istio.io"envoyfilter实现
cat << EOF > ef-from-notrequestPrincipals.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- urlPath:
path:
exact: /productpage
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.principal
value:
stringMatch:
exact: testing@secure.istio.io/testing@secure.istio.io
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-notrequestPrincipals.yaml -n istio --context context-cluster1from-namespaces
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- from:
- source:
namespaces:
- "istio-system"envoyfilter实现
cat << EOF > ef-from-namespaces.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-namespaces.yaml -n istio --context context-cluster1from-notNamespaces
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- from:
- source:
notNamespaces:
- "test"envoyfilter实现
cat << EOF > ef-from-notNamespaces.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/test/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-notNamespaces.yaml -n istio --context context-cluster1from-ipBlocks
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: ingressgateway
spec:
selector:
matchLabels:
app: istio-ingressgateway
action: ALLOW
rules:
- from:
- source:
ipBlocks:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-from-ipBlocks.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: istio-ingressgateway
configPatches:
- applyTo: HTTP_FILTER
match:
context: GATEWAY
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio-system]-policy[ingressgateway]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- directRemoteIp:
addressPrefix: 172.20.0.0
prefixLen: 16
EOF
kubectl apply -f ef-from-ipBlocks.yaml -n istio-system --context context-cluster1from-notIpBlocks
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: ingressgateway
spec:
selector:
matchLabels:
app: istio-ingressgateway
action: ALLOW
rules:
- from:
- source:
notIpBlocks:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-from-notIpBlocks.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: istio-ingressgateway
configPatches:
- applyTo: HTTP_FILTER
match:
context: GATEWAY
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio-system]-policy[ingressgateway]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- directRemoteIp:
addressPrefix: 172.20.0.0
prefixLen: 16
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-notIpBlocks.yaml -n istio-system --context context-cluster1from-remoteIpBlocks
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: ingressgateway
spec:
selector:
matchLabels:
app: istio-ingressgateway
action: DENY
rules:
- from:
- source:
remoteIpBlocks:
- 192.168.198.1/32envoyfilter实现
cat << EOF > ef-from-remoteIpBlocks.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: istio-ingressgateway
configPatches:
- applyTo: HTTP_FILTER
match:
context: GATEWAY
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
action: DENY
policies:
ns[istio-system]-policy[ingressgateway]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- remoteIp:
addressPrefix: 192.168.198.1
prefixLen: 32
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-from-remoteIpBlocks.yaml -n istio-system --context context-cluster1from-notRemoteIpBlocks
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: ingressgateway
spec:
selector:
matchLabels:
app: istio-ingressgateway
action: ALLOW
rules:
- from:
- source:
notRemoteIpBlocks:
- "192.168.198.1/32envoyfilter实现
cat << EOF > ef-from-notRemoteIpBlocks.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: istio-ingressgateway
configPatches:
- applyTo: HTTP_FILTER
match:
context: GATEWAY
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
- name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio-system]-policy[ingressgateway]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- remoteIp:
addressPrefix: 192.168.198.1
prefixLen: 32
EOF
kubectl apply -f ef-from-notRemoteIpBlocks.yaml -n istio-system --context context-cluster1to-hosts
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- to:
- operation:
hosts:
- "bookinfo.demo:30986"
from:
- source:
namespaces:
- "istio-system"envoyfilter实现
cat << EOF > ef-to-hosts.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- header:
name: :authority
safeRegexMatch:
googleRe2: {}
regex: (?i)bookinfo\.demo:30986
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-hosts.yaml -n istio --context context-cluster1to-notHosts
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- to:
- operation:
notHosts:
- "test"
from:
- source:
namespaces:
- "istio-system"envoyfilter实现
cat << EOF > ef-to-notHosts.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- header:
name: :authority
safeRegexMatch:
googleRe2: {}
regex: (?i)test
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-notHosts.yaml -n istio --context context-cluster1to-ports
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
ports:
- "9080"envoyfilter实现
cat << EOF > ef-to-ports.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
- name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- destinationPort: 9080
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-ports.yaml -n istio --context context-cluster1to-notPorts
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
notPorts:
- "9080"envoyfilter实现
cat << EOF > ef-to-notPorts.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- destinationPort: 8080
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-notPorts.yaml -n istio --context context-cluster1to-methods
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
methods:
- "GET"envoyfilter实现
cat << EOF > ef-to-methods.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: GET
name: :method
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-methods.yaml -n istio --context context-cluster1to-notMethods
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
notMethods:
- "GET"envoyfilter实现
cat << EOF > ef-to-notMethods.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- header:
exactMatch: GET
name: :method
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-notMethods.yaml -n istio --context context-cluster1to-paths
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
paths:
- "/details/0"envoyfilter实现
cat << EOF > ef-to-paths.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- urlPath:
path:
exact: /details/0
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-paths.yaml -n istio --context context-cluster1to-notPaths
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: details
spec:
selector:
matchLabels:
app: details
version: v1
action: ALLOW
rules:
- to:
- operation:
notPaths:
- "/details/0"envoyfilter实现
cat << EOF > ef-to-notPaths.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: details
version: v1
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[details]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- urlPath:
path:
exact: /details/0
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-to-notPaths.yaml -n istio --context context-cluster1when-request.headers-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.headers[test]
values:
- "test"envoyfilter实现
cat << EOF > ef-when-request.headers.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- header:
exactMatch: test
name: test
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.headers.yaml -n istio --context context-cluster1when-request.headers-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.headers[test]
notValues:
- "test"envoyfilter实现
cat << EOF > ef-when-request.headers-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- header:
exactMatch: test
name: test
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.headers-notvalues.yaml -n istio --context context-cluster1when-source.ip-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- when:
- key: source.ip
values:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-when-source.ip-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- directRemoteIp:
addressPrefix: 172.20.0.0
prefixLen: 16
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-source.ip-values.yaml -n istio --context context-cluster1when-source.ip-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- when:
- key: source.ip
notValues:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-when-source.ip-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- directRemoteIp:
addressPrefix: 172.20.0.0
prefixLen: 16
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-source.ip-notvalues.yaml -n istio --context context-cluster1when-remote.ip-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: DENY
rules:
- when:
- key: remote.ip
values:
- "192.168.198.1/32"envoyfilter实现
cat << EOF > ef-when-remote.ip-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
action: DENY
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- remoteIp:
addressPrefix: 192.168.198.1
prefixLen: 32
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-remote.ip-values.yaml -n istio --context context-cluster1when-remote.p-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- when:
- key: remote.ip
notValues:
- "192.168.198.1/32"envoyfilter实现
cat << EOF > ef-when-remote.ip-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- remoteIp:
addressPrefix: 192.168.198.1
prefixLen: 32
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-remote.ip-values.yaml -n istio --context context-cluster1when-source.namespace-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- when:
- key: source.namespace
values:
- "istio-system"envoyfilter实现
cat << EOF > when-source.namespace-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f when-source.namespace-values.yaml -n istio --context context-cluster1when-source.namespace-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
action: ALLOW
rules:
- when:
- key: source.namespace
notValues:
- "istio-system"envoyfilter实现
cat << EOF > ef-when-source.namespace-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-source.namespace-notvalues.yaml -n istio --context context-cluster1when-source.principal-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: source.principal
values:
- "cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"envoyfilter实现
cat << EOF > ef-when-source.principal-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
exact: spiffe://cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-source.principal-values.yaml -n istio --context context-cluster1when-source.principal-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: source.principal
notValues:
- "cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account"envoyfilter实现
cat << EOF > ef-when-source.principal-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- authenticated:
principalName:
exact: spiffe://cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-source.principal-notvalues.yaml -n istio --context context-cluster1when-request.auth.principal-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.principal
values:
- "testing@secure.istio.io/testing@secure.istio.io"envoyfilter实现
cat << EOF > ef-when-request.auth.principal-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.principal
value:
stringMatch:
exact: testing@secure.istio.io/testing@secure.istio.io
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.principal-values.yaml -n istio --context context-cluster1when-request.auth.principal-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.principal
notValues:
- "testing@secure.istio.io/testing@secure.istio.io"envoyfilter实现
cat << EOF > ef-when-request.auth.principal-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.principal
value:
stringMatch:
exact: testing@secure.istio.io/testing@secure.istio.io
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.principal-notvalues.yaml -n istio --context context-cluster1when-request.auth.audiences-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.audiences
values:
- "app"
- "web"envoyfilter实现
cat << EOF > ef-when-request.auth.audiences-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.audiences
value:
stringMatch:
exact: app
- metadata:
filter: istio_authn
path:
- key: request.auth.audiences
value:
stringMatch:
exact: “web”
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.audiences-values.yaml -n istio --context context-cluster1when-request.auth.audiences-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.audiences
notValues:
- "app"
- “web”envoyfilter实现
cat << EOF > ef-when-request.auth.audiences-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.audiences
value:
stringMatch:
exact: app
- metadata:
filter: istio_authn
path:
- key: request.auth.audiences
value:
stringMatch:
exact: “web”
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.audiences-notvalues.yaml -n istio --context context-cluster1when-request.auth.presenter-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.presenter
values:
- "app"envoyfilter实现
cat << EOF > ef-when-request.auth.presenter-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.presenter
value:
stringMatch:
exact: app
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.presenter-values.yaml -n istio --context context-cluster1when-request.auth.presenter-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.presenter
notValues:
- "app"envoyfilter实现
cat << EOF > ef-when-request.auth.presenter-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.presenter
value:
stringMatch:
exact: app
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.presenter-notvalues.yaml -n istio --context context-cluster1when-request.auth.claims-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.claims[groups]
values:
- "group1"envoyfilter实现
cat << EOF > ef-when-request.auth.claims-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.claims
- key: groups
value:
listMatch:
oneOf:
stringMatch:
exact: group1
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.claims-values.yaml -n istio --context context-cluster1when-request.auth.claims-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: request.auth.claims[groups]
notValues:
- "group1"envoyfilter实现
cat << EOF > ef-when-request.auth.claims-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- any: true
principals:
- andIds:
ids:
- notId:
orIds:
ids:
- metadata:
filter: istio_authn
path:
- key: request.auth.claims
- key: groups
value:
listMatch:
oneOf:
stringMatch:
exact: group1
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-request.auth.claims-notvalues.yaml -n istio --context context-cluster1when-destination.ip-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: destination.ip
values:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-when-destination.ip-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- destinationIp:
addressPrefix: 172.20.0.0
prefixLen: 16
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-destination.ip-values.yaml -n istio --context context-cluster1when-destination.ip-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: destination.ip
notValues:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-when-destination.ip-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- destinationIp:
addressPrefix: 172.20.0.0
prefixLen: 16
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-destination.ip-notvalues.yaml -n istio --context context-cluster1when-destination.port-values
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: destination.port
values:
- "9080"envoyfilter实现
cat << EOF > ef-when-destination.port-values.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- destinationPort: 9080
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-destination.port-values.yaml -n istio --context context-cluster1when-destination.port-notvalues
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: destination.port
notValues:
- "9080"envoyfilter实现
cat << EOF > ef-when-destination.port-notvalues.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- destinationPort: 9080
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-destination.port-notvalues.yaml -n istio --context context-cluster1when-connection.sni-value
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: connection.sni
values:
- "outbound_.9080_._.productpage.istio.svc.cluster.local"envoyfilter实现
cat << EOF > ef-when-connection.sni-value.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- requestedServerName:
exact: outbound_.9080_._.productpage.istio.svc.cluster.local
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-connection.sni-value.yaml -n istio --context context-cluster1when-connection.sni-notvalue
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
selector:
matchLabels:
app: productpage
version: v1
action: ALLOW
rules:
- when:
- key: connection.sni
notValues:
- "outbound_.9080_._.productpage.istio.svc.cluster.local"envoyfilter实现
cat << EOF > ef-when-connection.sni-notvalue.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- notRule:
orRules:
rules:
- requestedServerName:
exact: outbound_.9080_._.productpage.istio.svc.cluster.local
principals:
- andIds:
ids:
- any: true
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-when-connection.sni-notvalue.yaml -n istio --context context-cluster1组合配置
authorizationPolicy实现方式
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: productpage
spec:
action: ALLOW
rules:
- from:
- source:
principals:
- cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account
namespaces:
- istio-system
to:
- operation:
methods: ["GET"]
paths: ["/productpage"]
- operation:
methods: ["GET"]
paths: ["/static/*"]
- operation:
methods: ["GET"]
paths: ["/api/v1/products/*"]
- operation:
methods: ["GET"]
paths: ["/logout"]
- operation:
methods: ["POST"]
paths: ["/login"]
when:
- key: source.ip
values:
- "172.20.0.0/16"envoyfilter实现
cat << EOF > ef-combine.yaml
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: match
spec:
workloadSelector:
labels:
app: productpage
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 9080
filterChain:
destinationPort: 9080
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.rbac
typedConfig:
'@type': type.googleapis.com/envoy.extensions.filters.http.rbac.v3.RBAC
rules:
policies:
ns[istio]-policy[productpage]-rule[0]:
permissions:
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: GET
name: :method
- orRules:
rules:
- urlPath:
path:
exact: /productpage
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: GET
name: :method
- orRules:
rules:
- urlPath:
path:
prefix: /static/
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: GET
name: :method
- orRules:
rules:
- urlPath:
path:
prefix: /api/v1/products/
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: GET
name: :method
- orRules:
rules:
- urlPath:
path:
exact: /logout
- andRules:
rules:
- orRules:
rules:
- header:
exactMatch: POST
name: :method
- orRules:
rules:
- urlPath:
path:
exact: /login
principals:
- andIds:
ids:
- orIds:
ids:
- authenticated:
principalName:
exact: spiffe://cluster.local/ns/istio-system/sa/istio-ingressgateway-service-account
- orIds:
ids:
- authenticated:
principalName:
safeRegex:
googleRe2: {}
regex: .*/ns/istio-system/.*
- orIds:
ids:
- directRemoteIp:
addressPrefix: 172.20.0.0
prefixLen: 16
shadowRulesStatPrefix: istio_dry_run_allow_
EOF
kubectl apply -f ef-combine.yaml -n istio --context context-cluster1

 Asynq任务框架
Asynq任务框架 MCP智能体开发实战
MCP智能体开发实战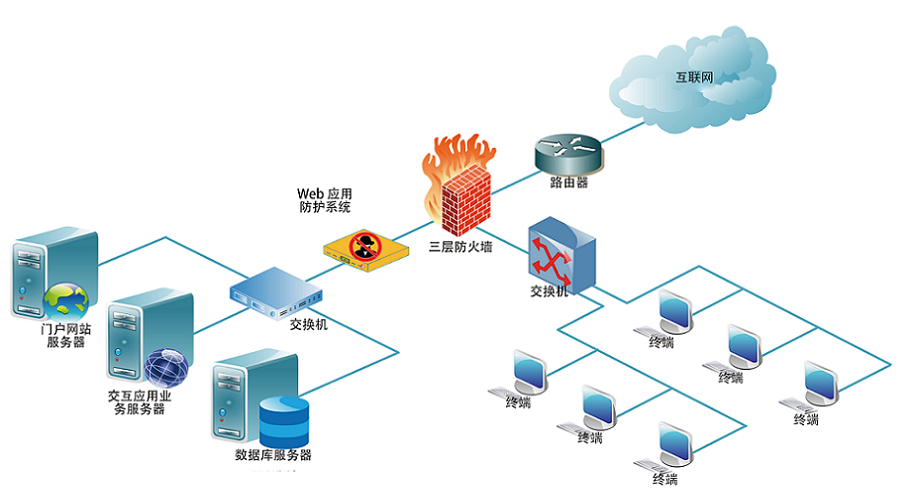 WEB架构
WEB架构 安全监控体系
安全监控体系